Several solutions are possible today, each with their advantages and drawbacks, allowing external workers access to company resources over a Wide Area Network (WAN), invariably through the company's firewall.
Problems with the Current Client-Server Architecture
In the current ENOVIA client-server architecture, client applications contact the servers using GIOP protocols(proprietary Orbix protocol or standard IIOP) which require a different port for each server to be contacted.
The current CORBA-based client-server architecture is as follows (the number of servers illustrated is not exhaustive):
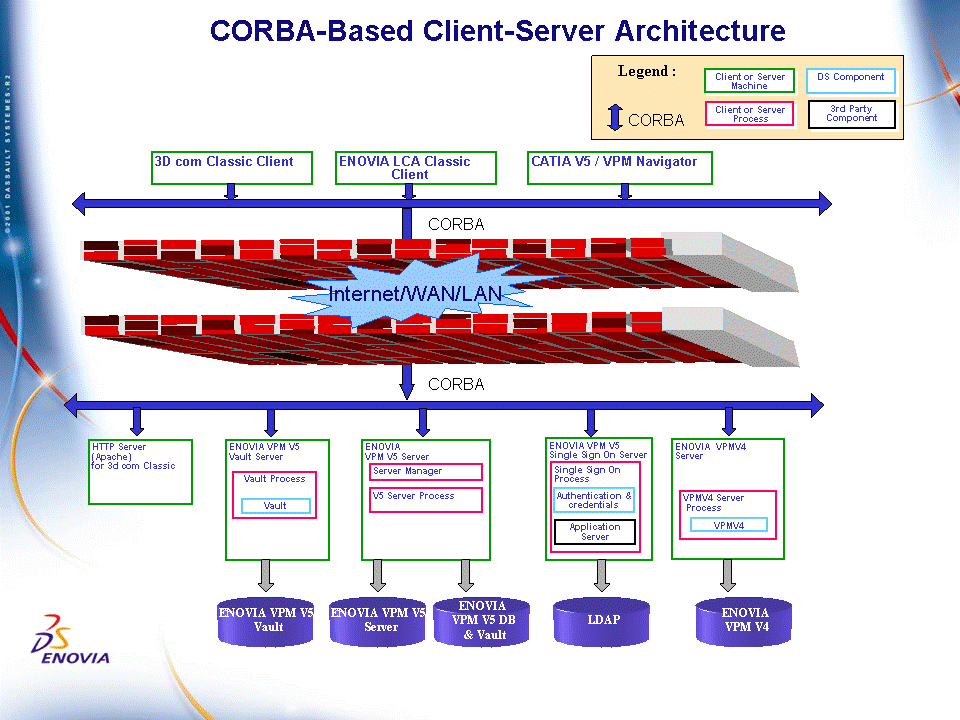
The drawbacks of the current solution are:
- complexity: using a CORBA-based architecture, there are too many ports to open/manage
- security: client logon userids and passwords sent over the Internet are not encrypted, representing a security threat
- latency: client-server communications over the Internet are affected by latency
- incompatibility: reverse proxies are not compatible with Corba, leading to complexity due to the high number of machines involved.
ENOVIA V5 VPM
Clients log on the servers by first contacting the Orbix daemon orbixd. The Server Manager is started, followed by one ENOVIA V5 VPM server per user. One Settings server per user and the Workbook server are also started. From the beginning, we have up to five different ports being used.
In some common scenarios, client applications need also to contact a vault server on a different host where another Orbix daemon is running. This requires using two additional ports.

ENOVIA 3d com Classic
Clients log on the servers by first contacting the Orbix daemon orbixd. The Server Manager is started, followed by the Workbook server and the Settings server. From the beginning, we have up to four different ports being used:
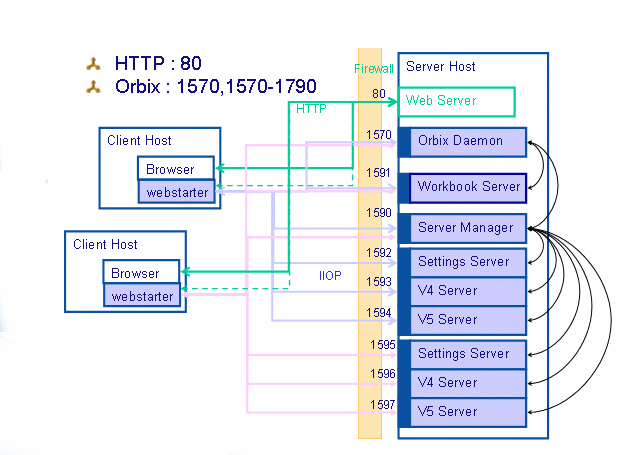
This architecture is well adapted to LANs (Local Area Networks) and Intranets, in which client and server hosts can connect to each other directly without going outside the corporate network. This is not the case for WANs (Wide Area Networks) and Extranets, in which client and server hosts have to cross network devices such as gateways and firewalls to connect to each other. The role of these (hardware or software) devices is to guard the borders of the corporate network from the Internet by enforcing rules controlling which client host (IP address) can connect to which server host (IP address) on which port.
To continue working, the above architecture supposes that a wide range of ports (currently 200) are open both on the client-side firewall (to enable outgoing connections to known server hosts on authorized ports) and on the server-side firewall (to allow incoming connections from known client hosts on authorized ports). This is problematic in terms of security and administration.
Basic Setup Solutions
There are currently two solutions for crossing Wide Area Networks:
- Virtual Private Networks (VPN)
- HTTP Tunneling.
Virtual Private Networks (VPN)
A Virtual Private Network (VPN) is a solution for securing communications through the public Internet.
Advantages
Attractions of VPNs to enterprises include:
- due to shared facilities, may be cheaper than traditional routed networks over dedicated facilities
- can rapidly link enterprise offices, as well as small-and-home-office and mobile workers
- allow customization of security and quality of service as needed for specific applications.
Distributing VPNs to homes, telecommuters, and small offices may put access to sensitive information in facilities not as well protected as more traditional facilities. VPNs need to be designed and operated under well-thought-out security policies. Organizations using them must have clear security rules supported by top management. When access goes beyond traditional office facilities, where there may be no professional administrators, security must be maintained as transparently as possible to end users.
VPN solutions involve a strong sense of trust and are implemented when a company knows and trusts the VPN user.
Implementing a VPN involves setting up:
-
VPN client software on remote client machines
-
a VPN server within the company's premises.
There is a single dedicated port for the VPN server.
Drawbacks
The main drawback in using a VPN is the administration overheads involved in setting up and maintaining software on the VPN client machines.
Implementing VPNs
No software is provided with Version 5 to implement VPNs, but VPNs are supported.
VPNs are implemented using hardware and software provided by a VPN vendor. Please refer to the documentation provided by the VPN vendor for more information.
HTTP Tunneling
HTTP Tunneling is a technique by which communications performed using various network protocols are encapsulated using the HTTP protocol, the network protocols in question usually belonging to the TCP/IP family of protocols.
A HTTP tunnel is used most often as a means for communication from network locations with restricted connectivity – most often behind NATs, firewalls, or proxy servers, and most often with applications that lack native support for communication in such conditions of restricted connectivity.
This solution comes with its specific components and processes to be started on client and server hosts, and has its own advantages and constraints.
However, it requires that ONLY ONE additional port be open on the firewalls standing between the client and the server networks, instead of the wide range of ports used by GIOP-based protocols. This port can be chosen arbitrarily by the administrator of the server network (a default is provided) and the clients will comply with this choice to administrate their own network security.
Technically, the solution is based on port redirection performed in the TCP protocol layer: each connection to a given port is finally redirected to the tunneling port open on the firewalls. All GIOP-based communications will occur through this dedicated port.
Refer to Basic Setup for information about setting up HTTP tunneling for both ENOVIA V5 VPM and ENOVIA 3d com Classic.
Limitation: HTTP Tunneling can not be used with CATIA Interoperability with LCA. If CATIA Interoperability with LCA is planned to be used on a WAN, it should be used through a market VPN (Virtual Private Network).
3d com Classic
For 3d com Classic, note that for original HTTP-based communications between the 3d com client application (and browser) and the 3d com web server, another dedicated port is used (typically port 80). However, since this port is commonly open on firewalls for this kind of communications, there is nothing more to do as compared to the standard installation where the tunneling components are not used.
Warning: Apart from Intranet usage, you MUST use the HTTP tunneling solution. Any incidents relating to firewalls or proxies will not be taken into consideration.
Advantages
- The solution is quite easy to deploy and administrate: just one file to edit to activate port redirection, one client process to configure, and one server process to configure, start, and control
- No dedicated host needed on the server side: the server component runs on each server host thanks to small memory overhead
- Client and server components have no impact on application code
- Only HTTP packets cross the firewalls
- Support for HTTP proxy and reverse proxy servers
- It's possible to activate SSL security and encryption on the HTTP solution
- Strong authentication: support of public key cryptography and certificates
- Data confidentiality: only encrypted packets cross the network and the firewalls
- Data integrity: support of message digest algorithms
- Apart from SSL configuration, the secured solution is also easy to deploy and administrate: just one file to edit to activate port redirection, one client process to configure, and one server process to configure, start, and control.
Drawbacks
- An additional process is running on the client host. However, this process is automatically started. Nevertheless, it might require some control whenever the provided fail-over mechanism is out.
- CPU and network overheads on the client and server sides due to the additional handling of HTTP semantics
- SSL configuration: acquire a certificate for each server host, configure clients to accept the server certificate (Optionally: acquire a certificate for each client host, configure servers to accept the client certificate). The HTTP proxy server must allow the HTTP CONNECT method on the SSL port.
Advanced Setup Solutions
Optional, more advanced setup solutions are supported as described in Advanced Setup:
- forward and reverse proxies
- secured tunneling mode (SSL).
![]()